If you're a "normal" person that hasn't owned a magic kit since you were 12, you might not be aware that magic shops, like everything else these days, have moved online. From the old school Penguin Magic (who recommend using Netscape Navigator for the best experience) to the more "hip" sites like Ellusionist and Theory11, the latest magic is only a few clicks away.
So now, instead of driving 40 minutes to some cigarette-smoke-filled store on the third floor of an office building (or, heaven forbid, going to a library), you can just fire up a web browser and start learning "The World's Toughest Card Trick" without ever leaving your couch.
But maybe $10 (at time of writing) seems like a lot of money for one card trick. No worries, if you just Google the name, you'll find that it's available from other sites for considerably cheaper.
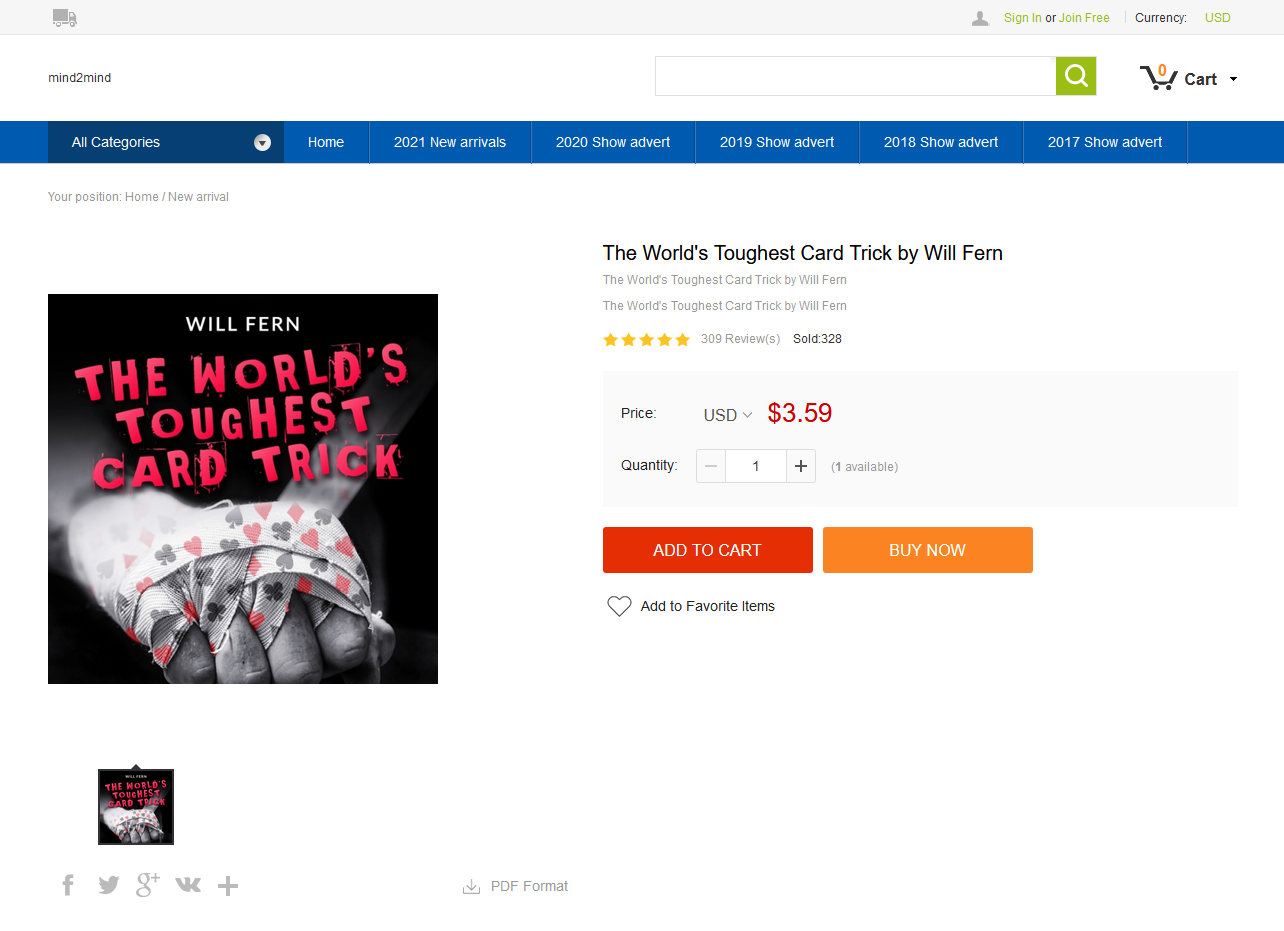
Wow, "mind2mind" has it for only $3.59, what a bargain!
Yarr!
If you saw that this post was about a "magic pirate" and were waiting for the spell-casting sailor to come into the story, then I'm sorry to disappoint you. Because yes, this site is selling stolen magic. How do I know? Two things:
- I mean, duh.
- This:
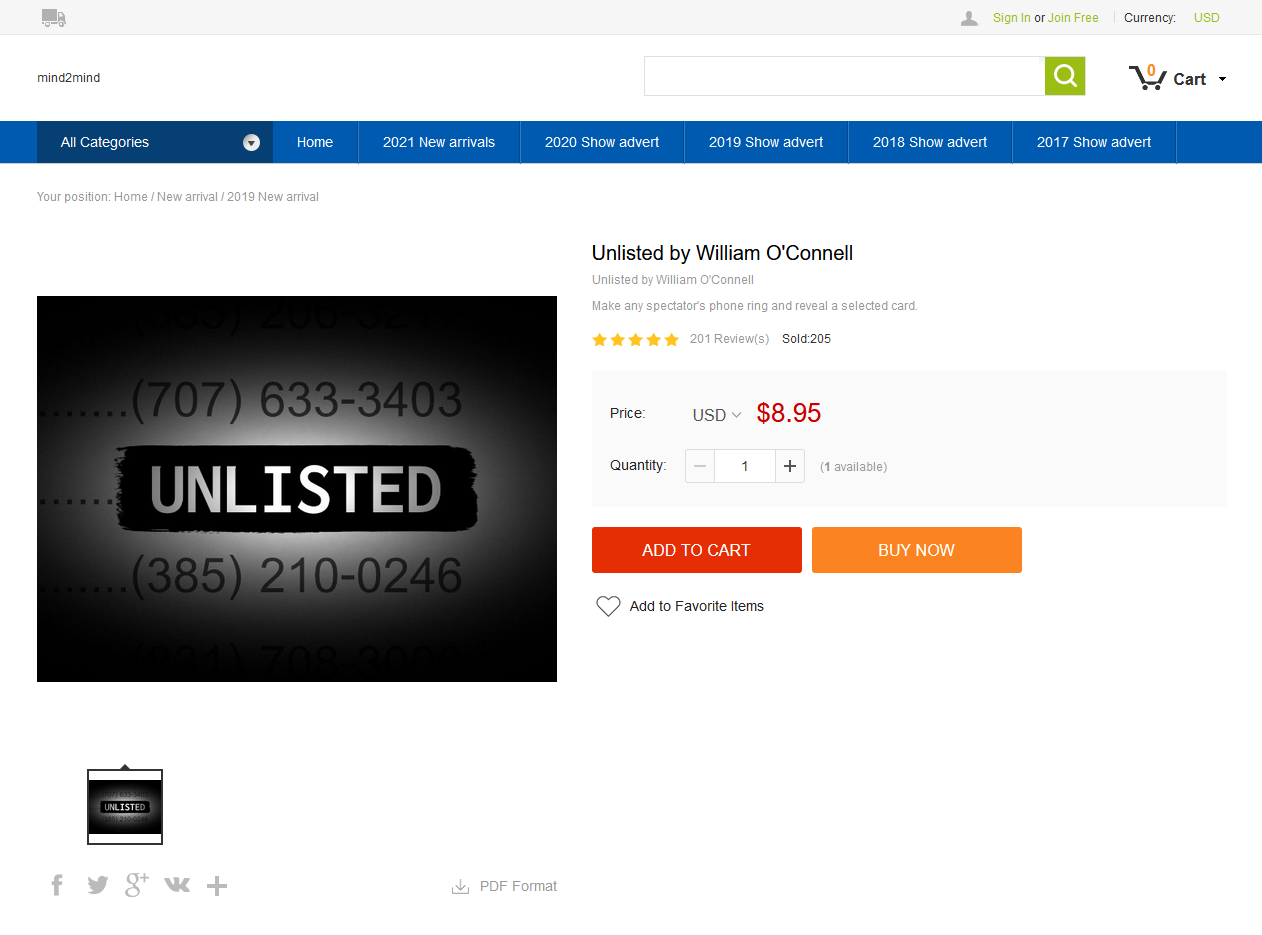
Yup, my trick, which normally goes for $24.99, is for sale on some website I've never heard of for less than $9. There are several of them, actually.
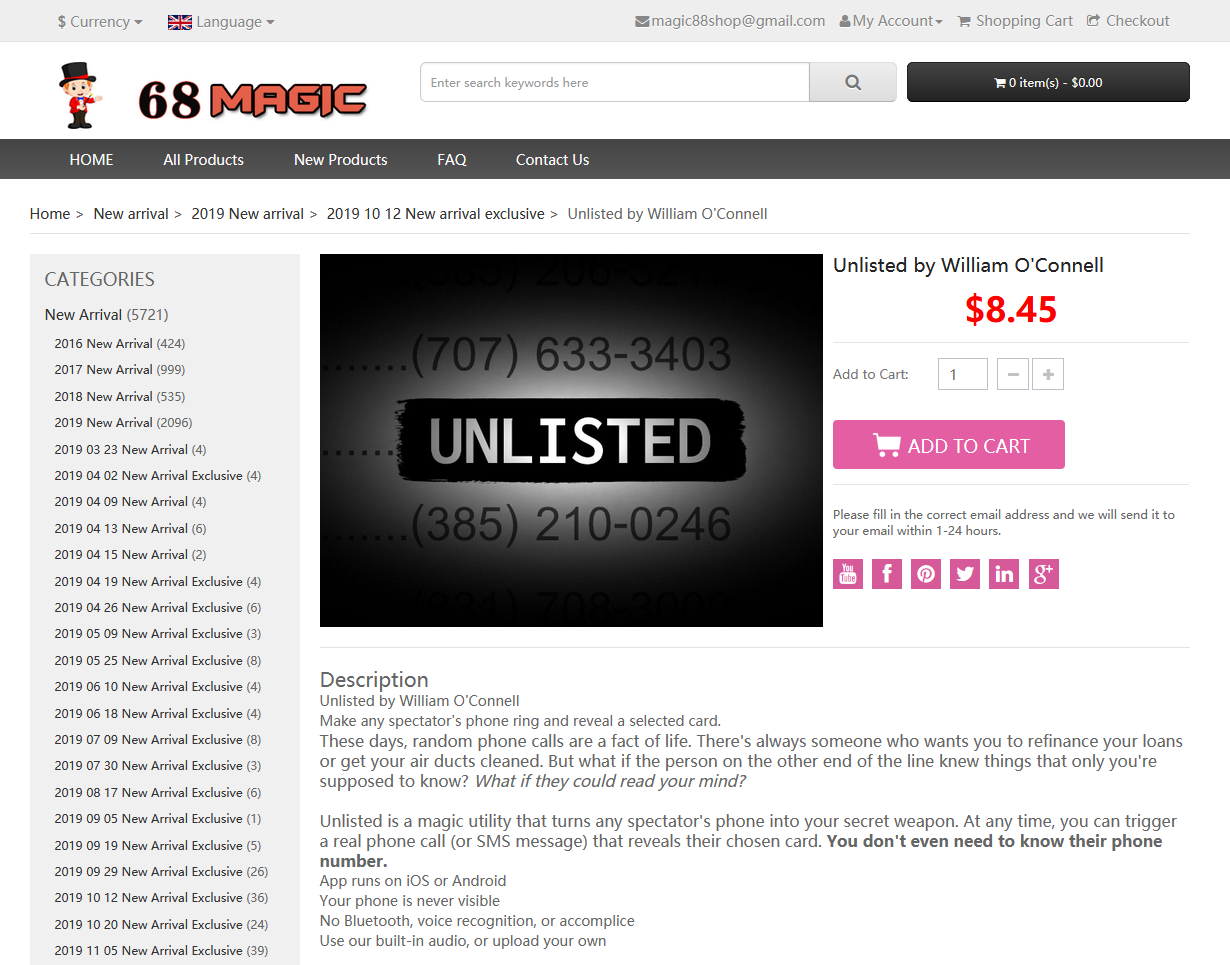
Extended Warranty, How Can I Lose?
A normal person's thought after seeing this might be something like "how dare they!" My first thought was "Huh, I wonder what happens when I buy it?"
See, you might assume that it's just a scam, where they take your money through some un-recoverable means and then never send you anything. On closer inspection that doesn't make a lot of sense though. Firstly, these sites only sell downloadable products, not anything that would require shipping. If the whole thing is just a lie, they'd have no need to restrict the inventory that way since they wouldn't actually have to ship anything regardless.
Secondly, they generally don't accept the kinds of cash-equivalent payment methods (Western Union, iTunes Gift Cards, etc.) that scammers use. I have seen a few that take Bitcoin, but by far the most common method is PayPal.
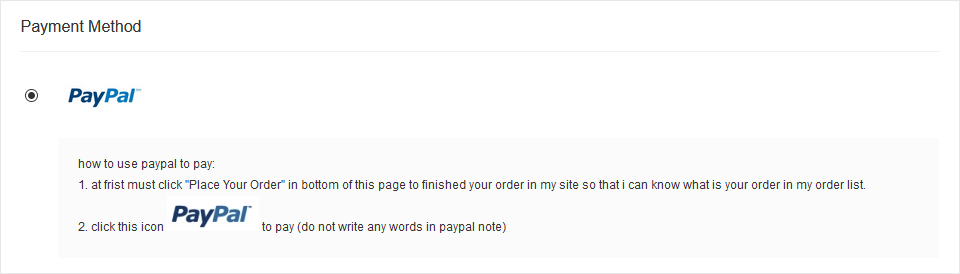
PayPal transactions can be hard to reverse in certain scenarios, but if you knew in advance that most of your customers would try to refund their purchase then it wouldn't be your first pick.
One Magic Please
I decided that the only way to satisfy my curiosity would be to actually put in an order for my own product, and see what (if anything) they would send me. To be clear: don't try this at home. I used burner contact and payment information, along with a VPN and some other safeguards. Even so, I'm sending money to criminals, which is generally a bad idea. But I had to know.
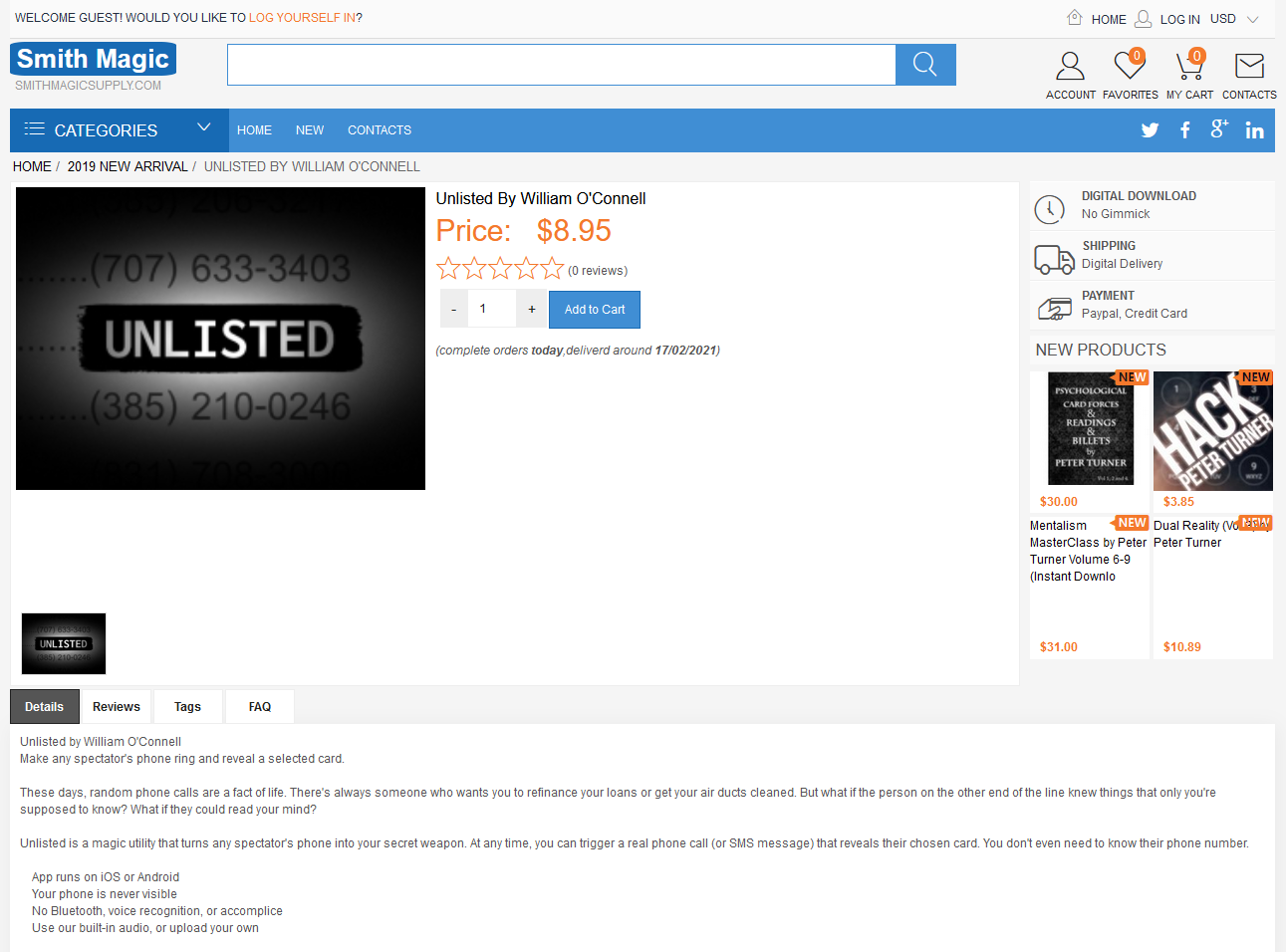
Buying something from these sites wasn't as easy as you'd think. The first one I tried, "Smith Magic", required an account but wouldn't let me create one. I then tried "Super Magic", which on reflection is pretty clearly the same website with a different name.

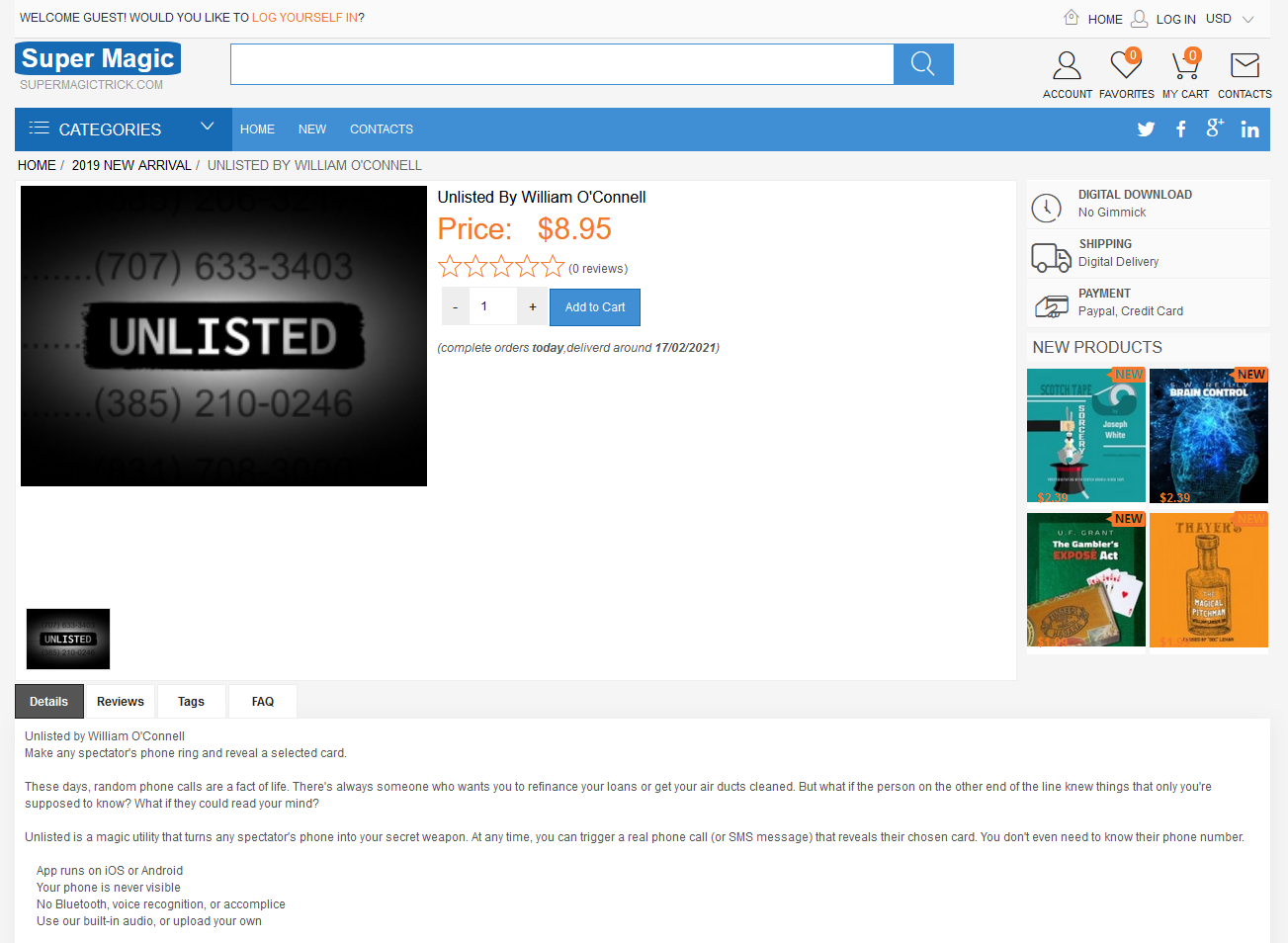
This time it let me make an account and check out, but the payment instructions said they'd email me a link to pay, which they never did. My order number was apparently "2" though, so it's possible they've never actually had a customer before.
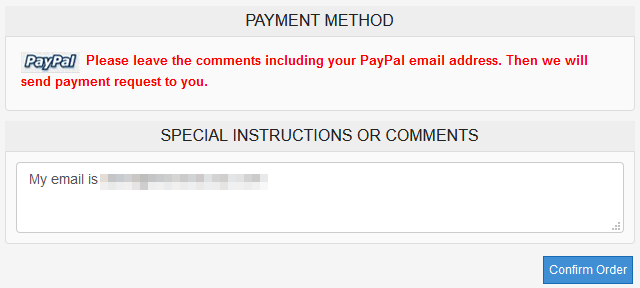

Having failed twice, I moved on to "68Magic", whose name I love because it suggests that they operate at least 67 more of these sites. The price there is actually 50 cents cheaper, at only $8.45. And they take normal credit/debit cards in addition to PayPal, although they seem to have a lot of rules regarding their use:
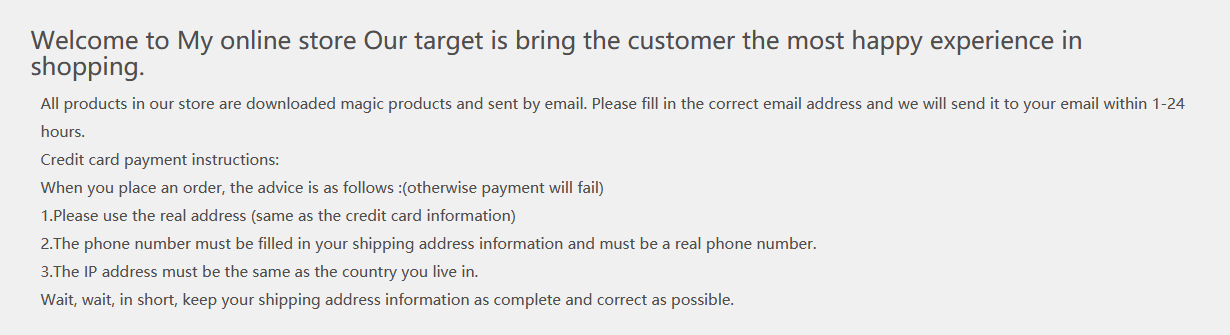
In theory none of that should have mattered, since my burner credit card doesn't have a specific billing address, but for whatever reason it wouldn't go through:

Luckily, they actually have a PayPal business account (rather than the personal paypal.me link that a lot of these sites use) so I was able to use my same card through there, which worked fine.
It was a regular first/last name in Chinese.
You've Got Mail
Around 8 hours later, I got an email.
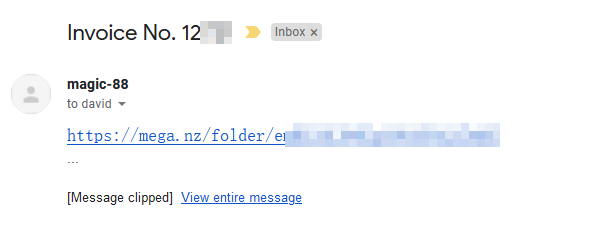
This must've been manually sent, since it took so long and came from an @qq.com email address (Tencent's webmail service). But there's no signature, no "thank you for your order", nothing but a Mega link. I guess if you change the name of your website every couple weeks then customer service isn't a priority. But hey, they did indeed send me something. And I was pretty shocked by what it was.
For context, Unlisted is an app that allows you to make someone else's phone ring and play a recorded message, without knowing their phone number. When you buy it legitimately, you receive a PDF explaining how to install it on your phone, as well as a product key that you use to create your account. Once you're signed in, the app has an instructions page that tells you how to actually perform with it.
Unlisted is available on its own website, as well as from Penguin and a few other legitimate third-party retailers. Looking at the knock-off sites, it's clear that the product descriptions are copied from Penguin, since that description is slightly different than the one on my own site. These knock-off sites have thousands of tricks on them, so I figured they'd probably found some sort of exploit for Penguin that allows them to download the tutorials en masse without paying for them. I think things like that have happened in the past, but it turns out that's not what happened to me.
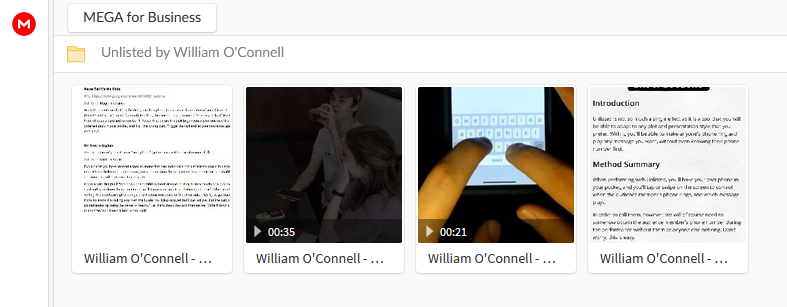
The Mega link contains four files. The first one is the PDF that I include with the trick giving some ideas on different ways to present it in a routine. The second file is the trailer video, which seems kind of pointless but whatever. The last two are where it gets interesting. Rather than the information about how to install it, you get a PDF capture of the performance instructions from inside the actual app. That means someone must have purchased my trick legitimately, created an account, then manually captured the instructions page. They even ripped the little video that shows which buttons to press.
And as it turns out, I know who it was.
See, there's a part of the instructions where it mentions a URL. That URL is unique for each user. Whoever made this PDF clearly knew that, because they drew a black rectangle over that part of the text.
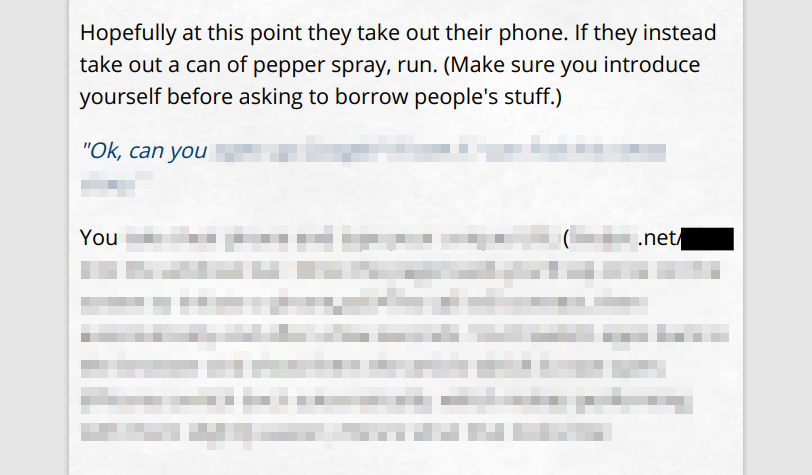
If you remember the Snowden NSA leaks, then you know where this is going. PDFs aren't just images, they contain the actual text of the document along with information about fonts, formatting, etc. When you draw a black box over part of the document, the text underneath is still part of the file, and you can read it by copy/pasting somewhere else. So I was able to read the redacted URL, which told me which account the screenshot had come from.
Ironically, the black bar itself reveals the screenshotter's identity as well. It turns out that it's a PDF "annotation", made using MacOS's built in tool which adds the author's name to the annotation metadata by default.
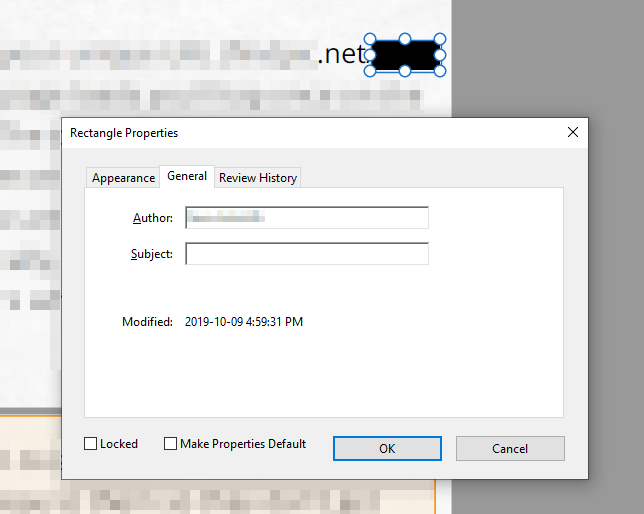
I won't share their name here, but it was actually someone I know. They're not a super close friend or anything, but we've talked online a few times. They purchased Unlisted legitimately, and as far as I know they're pretty strongly against piracy. They're also not in China, so clearly there's more to the story of how these files ended up where they did.
I reached out to them, and they said they didn't even remember having made the PDF, but they later found it in their backup files. From what they told me, it sounds like at some point they sent the PDF to a friend who was looking for information about the trick, and from there it ended up in some big collection of magic torrents. They could be lying of course, but I don't find that story entirely implausible, and in any case that's all the information they gave me.
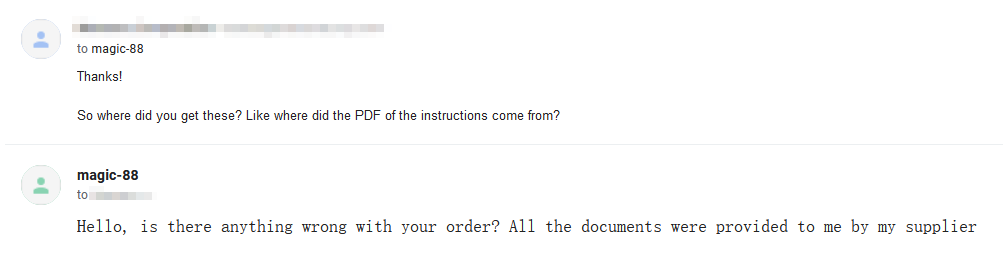
I did try just asking 68Magic where they got the files, but you'll be shocked to hear that they weren't very helpful.
Who Are You People
So who runs these websites? 68Magic's footer actually lists a physical address in Guangzhou, which appears to be some kind of giant office building, but I couldn't find much information about it. I suppose they could have some sort of office or P.O. box there, but it also seems like exactly the kind of place you'd pick if you were going to just make up an address.

I did try looking up the name from the PayPal account, but it's not a very unique name and again I don't have any way to know if it's real, stolen, or just made up.
The site (and even the HTML source code underlying it) doesn't contain any obvious references to a specific CMS, but based on some of the CSS class names and URL formats I determined that they're using the open source Zen Cart e-commerce system.
The domain for 68magic.com is registered with eName, a Chinese registrar who are reasonably legit from what I can tell. The IP address points to WorldStream, an IaaS provider in The Netherlands who are apparently fairly popular for torrent seedboxes and the like.
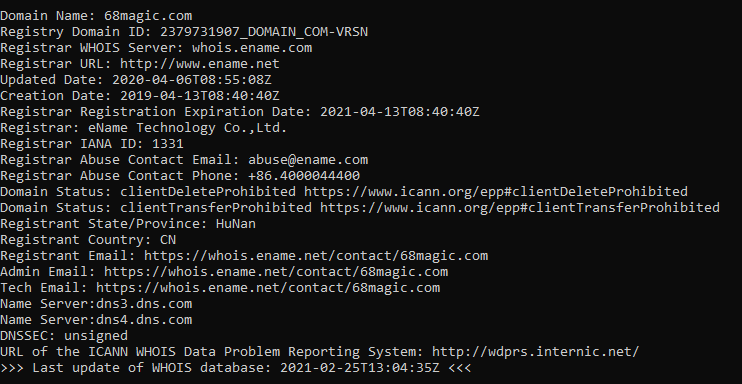

Not all of the sites are the same, though. Super Magic (the one that never sent me a payment form) also uses Zen Cart, but their domain is registered with GoDaddy. Their site uses CloudFlare's CDN, so the server's IP address isn't public, but GoDaddy told me they're just the registrar and not the host. Meanwhile "mind2mind" seems to be registered and hosted through Alibaba Cloud.
The differences in site design, payment method, and hosting suggest that the sites are run by different owners. It makes me wonder if somewhere on the internet there are people sharing tips for how to set up your own pirated magic store.
I didn't find anything exactly like that on the Zen Cart forums, but I did find this post, in which someone complains about problems with what appears to be that same payment processor that told me to "pay again".
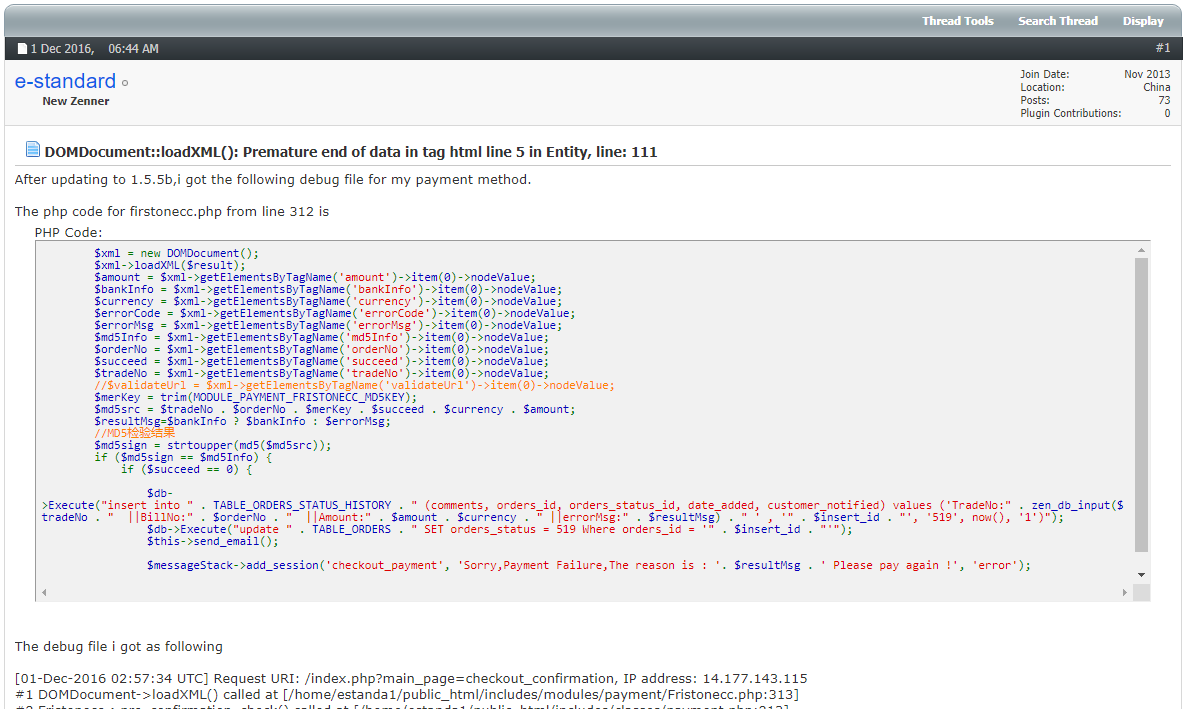
And what site are they using it on?
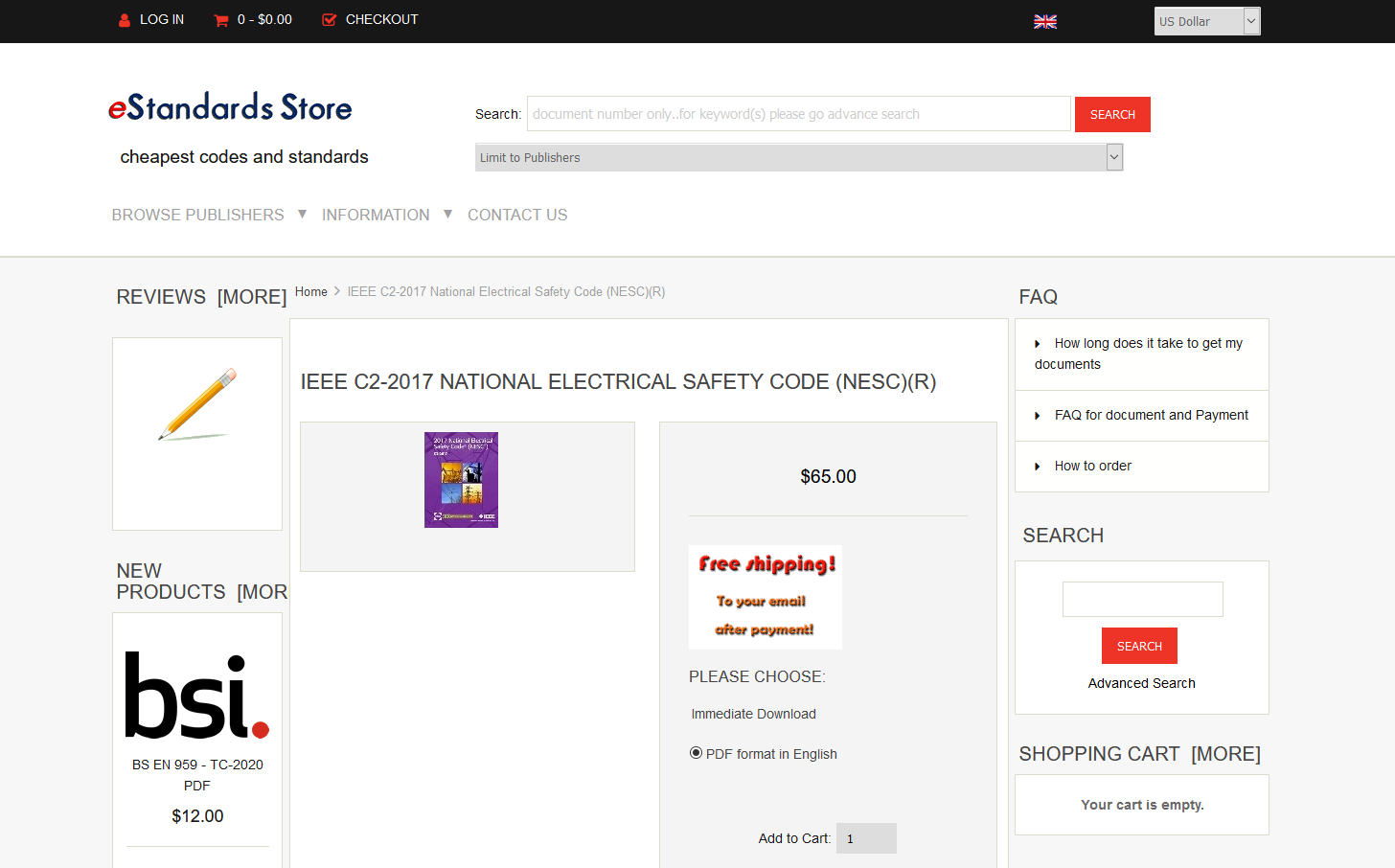
It's a website that sells PDFs of technical standards for suspiciously low prices (this one would cost around $200 if purchased from the IEEE directly). So basically the same thing as the magic sites, just a different industry. Fair enough.
No Need to Feel Down
Having done all the investigation I could (short of flying to China), I figured it was about time I sent out DMCA notices and moved on with my life. Apparently I'm not the first person to do so.
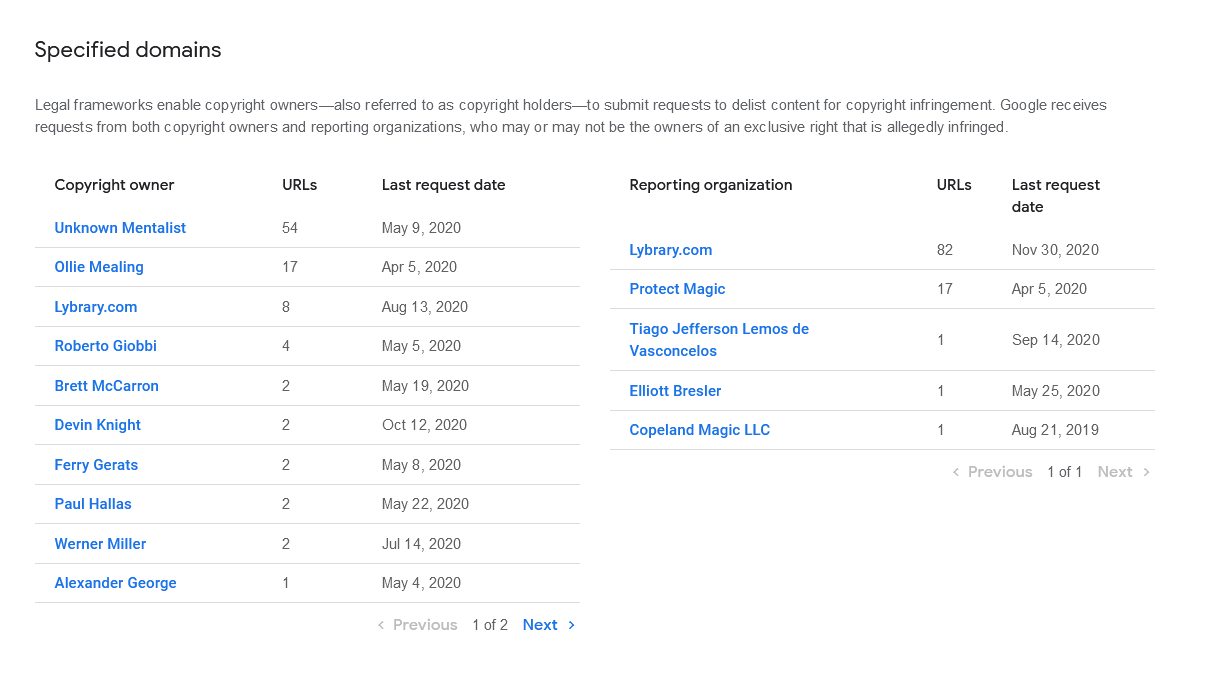
To their credit, Google and WorldStream processed my reports very quickly. CloudFlare never wrote me back explicitly, but Unlisted seems to have been removed from the sites they were proxying so maybe they passed my message along to the right people. For now, the first page of search results for my trick is free of scams, at least until this person moves on to "69Magic" (although that domain might already be used for... something else).
I do wonder if there's more that could be done though. If the images/text are all being ripped from Penguin, maybe they could be helping their creators detect these knock-off sites, or even issuing DMCA notices on their behalf. And if Google has gotten hundreds of complaints about a certain domain, why do they continue to rank it so highly in search results? Stolen magic tricks aren't a big deal in the scheme of things, but for how much time and effort goes into detecting music in the background of livestreams with 10 viewers, you'd think this kind of obvious theft would be harder to pull off.
So Remember Kids
What's the takeaway from all this? Well first of all, if you want to buy my magic trick you should get it from somewhere that will actually give you a product key. But more broadly:
- Building an online store is pretty easy these days
- No product is too low-volume for someone to knock off
- DMCA takedowns work, at least temporarily
- If at first you don't succeed, please pay again
If you have any additional information about any of this, or you think I got something wrong, let me know.